One of the most frequently occurring discussions around payment security is regarding PCI compliance. When we talk with our customers, partners and integrators, especially with those who are new to the payments industry, understanding PCI compliance can be complex.
The PCI DSS, for example, refers to the Data Security Standard released by the PCI Council that are set up to ensure that all businesses that accept, process, store and/ or transmit cardholder data (i.e., credit card information), do it in the safest way possible. By following the DSS and other related standards, merchants can better protect their payment infrastructures from data breaches. They not only keep customer data safe but also protect their brand reputation.
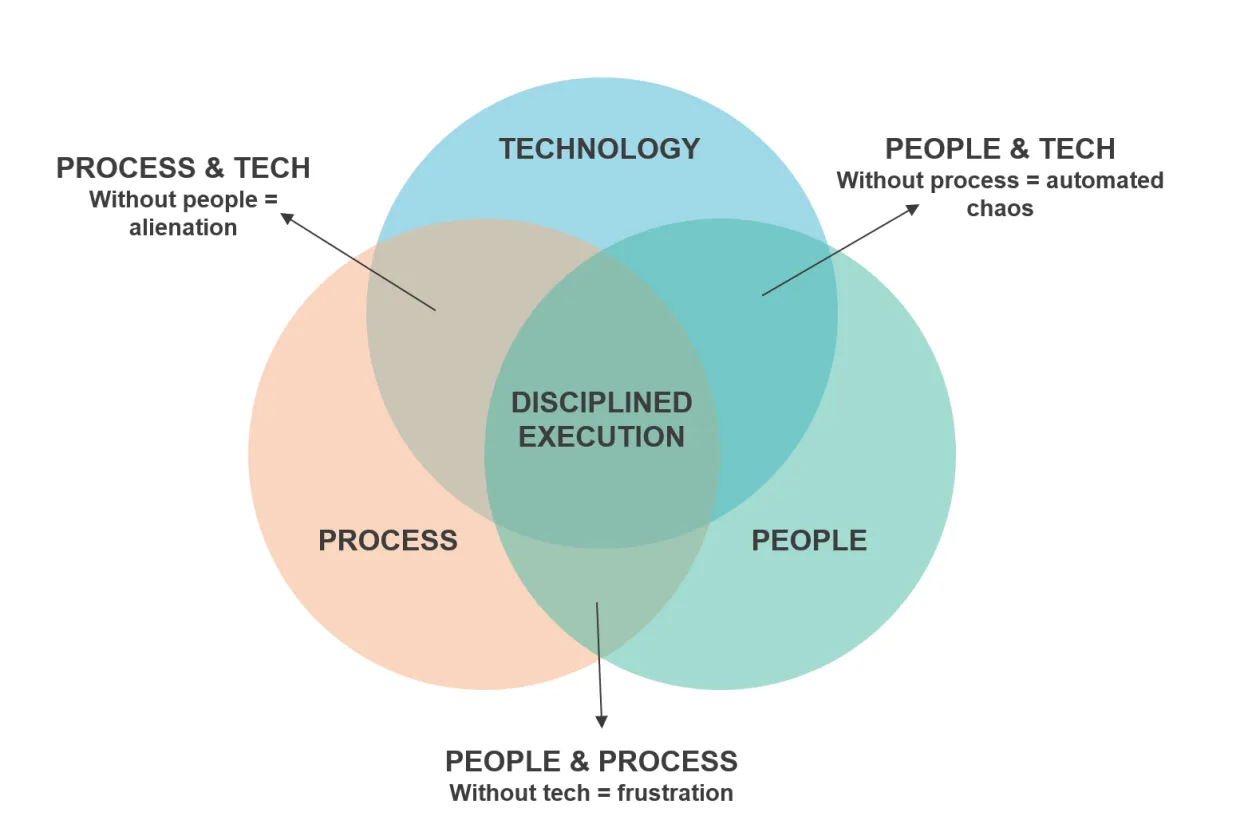
In 2020, 37 billion records were compromised in publicly disclosed breaches, and with 2021 more than halfway done, merchants and their solutions providers need to consider, not only achieving PCI compliance but how to more easily maintain that assurance on a daily basis. Cybercriminal activities are constantly evolving and becoming more sophisticated and businesses need to take additional security measures to protect sensitive cardholder data and their payment technology solutions. This can be achieved with a balanced security approach that limits the footprint of where sensitive data exists in your network. This is referred to as “limiting your attack surface” and is a fundamental best practice when it comes to securing your payment infrastructure that pulls together three main elements: technology, process and people.
Let's consider the first element; “Technology”. This refers to solutions that can help businesses add more layers to their payment environment making it very difficult for cybercriminals to steal sensitive information. These solutions can range from encryption software to other semi-integrated environments that help isolate the payment process and more.
Semi-Integrated Payment Approach
A semi-integrated approach reduces the communication between the terminal and the electronic cash register (ECR) to non-sensitive commands. Sensitive card information is isolated, encrypted and directly sent from the payment terminal to the intended processing hosts or gateway. This way, the payment card data never touches the point of sale (POS) system keeping it safe from any vulnerabilities and potential cyberattacks. The semi-integrated approach also keeps the POS system out of the PCI audit scope, saving businesses time and money when it comes to certifying these solutions.
Point-to-Point Encryption (P2PE)
Payment data can be stolen in many ways and a common way these thefts happen is when the data is in transit from one point to another. A P2PE solution helps protect the card data while it is on the move during the payment process. It is an industry-proven solution that helps protect sensitive card data from cybercriminals. It encrypts this sensitive data which can only be accessed with a decryption key – making the data, if stolen, useless to the criminal.
Tokenization
To complement P2PE, tokenization helps protect the card data at rest. It replaces the sensitive information with a secure token protecting it from cybercriminals. With many data breaches over the last decade, current PCI standards do not allow businesses to save and store credit card details unless they are tokenized on their POS system or databases after a transaction. If the open data is stored and is stolen, it can be used to create counterfeit cards. When this data is tokenized, it becomes useless to any cybercriminal as it can only be decoded by the payment processor. Storing tokenized data helps retailers associate these tokens to specific customers and can further enable them to study spending patterns without compromising the security of sensitive credit card information.
Balanced Security Approach
Security threats are always evolving and so will the solutions to fight them. Businesses must make themselves aware of these changes and developments to stay ahead of potential data breaches. However, these technology solutions are not the only part of a balanced security approach. In upcoming blog posts, I will talk through both “people” and “process” as important elements of your business’s security strategy.
If you are interested in learning more about protecting your payment technology investment and would like to speak with someone, drop us a line.
Steven Bowles is the Regional Security Officer & Director of Security Solutions at Ingenico