Are Android terminals safe? 5 key principles driving payment security on Ingenico’s AXIUM platform

Ingenico has an essential philosophy at its core - to stay up to date with the latest security standards and promote the most secure cryptographic elements for our customers.
These principles lie at the foundation of Ingenico’s approach to developing its solutions, including those using Android. This point is perfectly illustrated by the recently launched AXIUM platform, which was designed to provide secure payment alongside the Android environment.
But whilst significant progress has been made in Android security in recent years, the following key principles remain vital to ensure a safe, secure, and trusted ecosystem:
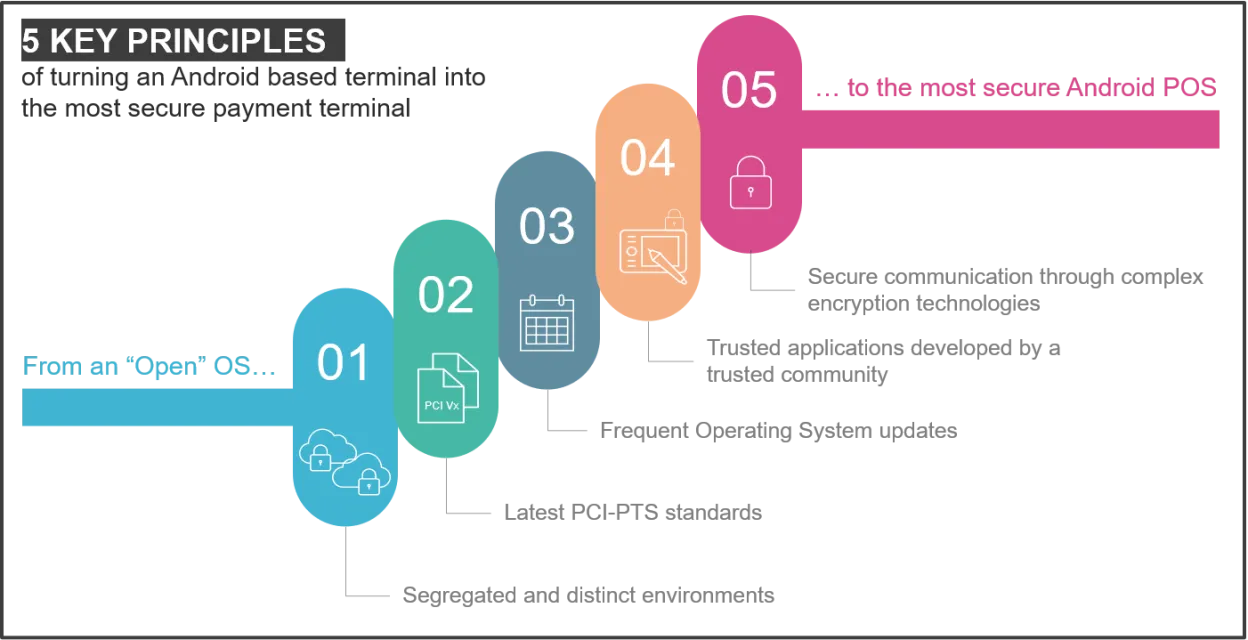
1. SEGREGATED AND DISTINCT ENVIRONMENTS BETWEEN EVERYTHING RELATED TO PAYMENT, AND NON-PAYMENT ASPECTS OF THE PLATFORM
Android applications created for consumer devices are usually published on Google Play™, the public Appstore managed by Google. Google provides developers with a set of tools to sign their application allowing the Google Play service to recognise and validate the signed software. This is needed to give the ‘green light’ for the software’s distribution.
However, an application authorised with the Google signing toolchain cannot be loaded on an AXIUM terminal. Instead, Ingenico designed a complete ecosystem to manage AXIUM business applications, creating a security red line that connects an app through the software development kit (SDK) and signature tools to the Ingenico Appstore on the Terminal Estate Manager (TEM) for the software distribution.
Looking at this in more technical depth, the Ingenico SDK manages the PCI-PTS SRED (Secure Read and Exchange Data) compliance requirements for Point of Interaction devices, respecting the wide set of security rules required by the PCI Council standard. These include:
- Protection against attempts to disclose cryptographic information
- Uniqueness of the secured keys
- Avoidance of sensitive data retention
- Cryptographic protection of firmware updates and remote access
to name just a few…
All these features are commonly used by the payment application and are authorised by the signature tool during the application signature process. However, non-payment applications can be signed to run on AXIUM without access to the payment environment and to the secured memory areas.
Managed interaction between non-payment applications with payment services is also possible, driven by specific payment APIs under a ‘payment as a service’ model, whilst still meeting the security principles described.
2. THE CERTIFICATION OF TECHNOLOGY DEVELOPED TO THE LATEST PCI-PTS STANDARDS
The AXIUM operating system (OS) is proprietary designed and dedicated to payment use cases. This provides the right level of security for both the user experience and the customer environment and is totally separate to any business applications.
Based on this architecture, the AXIUM OS and the overall platform have been certified with the most recent certification, PCI PTS version 6.
However, compliance is only one aspect of platform security…
3. FREQUENT UPDATES, ENSURING THAT ANDROID POS, AND CONNECTED DEVICES, ARE PROTECTED FROM EVOLVING THREATS
Android is a giant with worldwide reach. It is no surprise therefore that it represents an appealing target for security threats. Whenever system weaknesses are discovered and resolved, or new security standards take shape, Android gets updated with security patches to prevent hacking or fraud. This is part of the natural life cycle of an operating system.
AXIUM is a business platform built on Android and has been designed to ensure the highest protection against any software threats. And just like Android, Ingenico has in place a continuous assessment process, to evaluate Android threats and solutions to keep AXIUM up to date, secure and trustworthy.
Compliance continues with updates to our customers’ estates supporting the terminal’s life cycle. One of the pillars of the AXIUM platform is that it is always connected. Through its proprietary Estate Manager platform (TEM), Ingenico delivers updates and security patches to AXIUM terminals seamlessly without interrupting the device. This ensures business continuity and provides the best performance to the end user without any compromise on security.
4. TRUSTED APPLICATIONS DEVELOPED BY PEOPLE WHO UNDERSTAND THE COMPLEX REGULATORY ENVIRONMENT
So, how do you protect the payment environment, (card readers, security, pin entry etc.) to ensure they meet the associated security restrictions whilst at the same time providing app developers with safe access to payment features?
This is achieved by preventing an application from directly accessing card payment peripherals, a key obstacle that would otherwise prevent the creation of generic applications. Indeed, Android applications that only use communication channels, screen and touch functions can be ported onto AXIUM quite effortlessly.
In this case, what really differentiates an AXIUM app from a standard Android app, is the signature process and software distribution that must be managed through Ingenico’s tools. This signing toolchain manages the Android permissions, according to the partnership level, thereby balancing the application approvals with the application’s purpose.
Third party app developers benefit from Ingenico’s Payment APIs which give them access to card payment features without getting involved in payment regulation complexity. The APIs provide the bridge to card payment processes in applications, leveraging Ingenico’s experience and opening up routes to new use cases.
The platform application signature scheme is designed to ensure that customers can build partnerships with third parties application providers, without interfering with the payment platform and its strong security constraints.
5. THE USE OF TERMINAL, ECOCSYSTEM, AND ENCRYPTION TECHNOLOGIES, TO ENSURE SECURE COMMUNICATION BETWEEN ALL PARTS OF THE PAYMENT AND SENSITIVE DATA CHAINS ARE PROTECTED, AND SAFELY INTEGRATED
ata protection may not be as fascinating or exciting as other aspects of a product, such as the design or user interface, but it sits at the core of a payment terminal and must withstand any threat: breaking the data protection wall would mean full access to sensitive information or money.
Sensitive data on a payment terminal is protected using cryptography. Commonly, cryptographic algorithms use one secret key (symmetric cryptography), or a pair of keys composed of a public/private key couple (asymmetric cryptography) to cipher and decipher data. The keys are secrets held by the parties allowed to safely exchange information, i.e., the credit card and the terminal.
As machine calculation performance grows over time, the main challenge for cryptographic algorithms is to keep secret keys complex enough to avoid reverse engineering (brute force attack resistance) whilst preserving quick data encryption/decryption processes. If a key is violated, this could allow access to data, such as transactions, credit cards, bank accounts, emails – all of which would be compromised, opening up the potential for users to become a victim of fraud.
The RSA key, (named after the surnames of Ron Rivest, Adi Shamir and Leonard Adleman, who first described the algorithm in 1977), is probably the most used asymmetric cryptographic algorithm in SSL/TLS communication security today: when we access a web portal or login to an authenticated service, RSA is working behind the scenes to prevent fraud and reduce risk.
However, research in cryptography continues to search for new concepts to solve the conundrum of fast encryption/decryption while preserving a strong key brute force resistance.
Elliptic Curve Cryptography (ECC) is one of the most enhanced asymmetric cryptographic algorithms and will probably replace RSA in time. ECC key pair generation is simple as private and public keys are a randomised point of an elliptic curve over a finite field. The ECC encryption algorithm, uses the elliptic curve math theory to cipher information. The reverse engineering of the ECC algorithm must solve a high-complexity math problem called “discrete logarithm over finite fields”: this reinforces the ECC brute force attack resistance, whilst reducing the key size and preserving a high level of performance in the encryption/decryption processes. For example, a proven elliptic curve cryptography key of 384 bit achieves the same level of security as an RSA key of 7680 bit.
The AXIUM platform is built with strong cryptography, including AES (Advanced Encryption Standard) symmetric keys and Elliptic Curve Cryptography (ECC). These security solutions are also compliant with the relevant security standards for PCI PIN and PCI P2PE.
All of the security elements described here are not only available on the AXIUM platform, but also on Ingenico’s Tetra platform too, helping to facilitate the integration, user experience and the overall estate management for our customers.
Ingenico’s proven experience in the payment industry has helped to bring together the benefits of all the latest technologies, cementing its position as a one of the world’s most trusted and reliable payment providers. We remain focused on our customer needs and will continue to work closely with them to deploy the latest features, guiding them through their use to ensure the most secure payment experience in new environments.
Security is in our DNA

If you would like to join Ingenico's Developer Community and learn more about building digital apps and services on our smart terminals, please visit our Developers' Partner Programme website.










